Securing Tomorrow: Quantum-Resistant Encryption Standards
Securing Tomorrow: Quantum-Resistant Encryption Standards
The Quantum Threat to Encryption
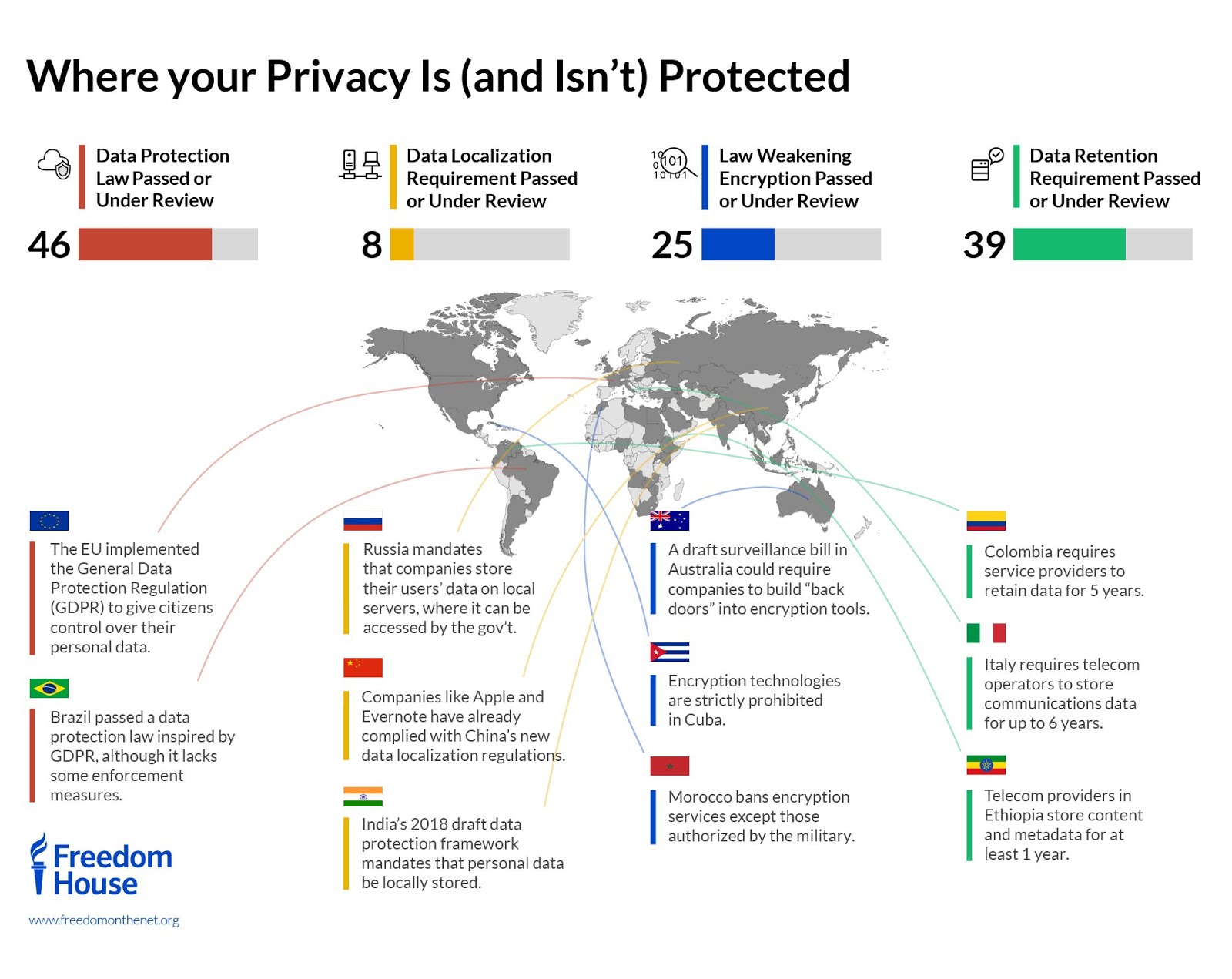
As quantum computers advance in capability, the threat they pose to traditional encryption methods becomes increasingly apparent. Quantum computers have the potential to break widely used encryption algorithms, rendering sensitive data vulnerable. Recognizing this quantum threat, the need for quantum-resistant encryption standards has become a critical focus in the field of cybersecurity.
Understanding Quantum Computing’s Impact
To comprehend the urgency of quantum-resistant encryption, it’s essential to understand how quantum computers differ from classical computers. Traditional encryption relies on complex mathematical problems that take classical computers considerable time to solve. Quantum computers, utilizing principles of superposition and entanglement, can perform these calculations exponentially faster, jeopardizing the security of current encryption standards.
The Vulnerability of Current Encryption
The encryption methods widely used today, such as RSA and ECC (Elliptic Curve Cryptography), rely on mathematical problems that quantum computers excel at solving. As quantum computing capabilities progress, the risk of adversaries decrypting sensitive information encrypted with these algorithms grows. Quantum-resistant encryption is imperative to stay ahead of potential cyber threats in the quantum era.
Quantum-Resistant Encryption: A Necessity
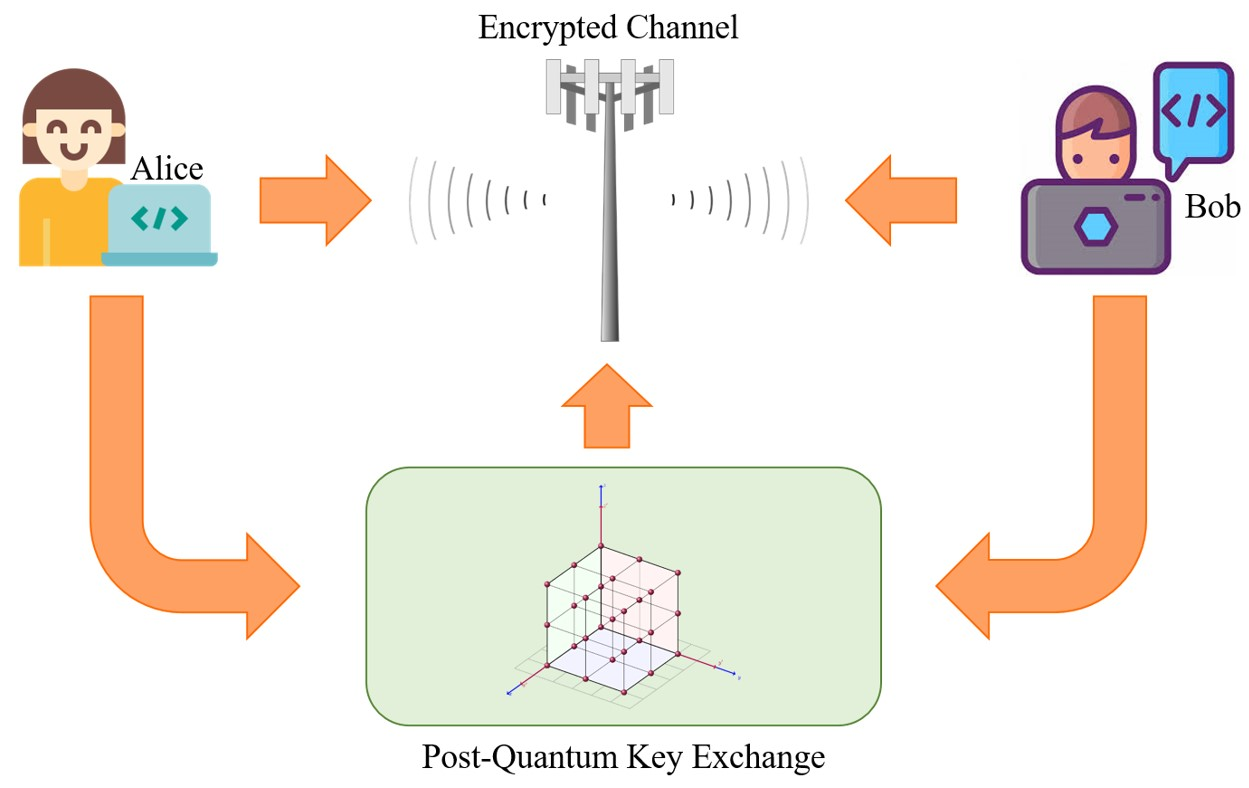
Quantum-resistant encryption standards aim to address the vulnerability posed by quantum computers. These standards employ cryptographic algorithms that remain secure even in the face of quantum attacks. Researchers and cybersecurity experts are actively developing and evaluating these quantum-resistant encryption methods to fortify the security of sensitive information against emerging quantum threats.
Post-Quantum Cryptography Research
The field of post-quantum cryptography involves the exploration of cryptographic algorithms that can withstand quantum attacks. Various approaches, including lattice-based cryptography, hash-based cryptography, and code-based cryptography, are being researched as potential candidates for quantum-resistant encryption standards. Rigorous evaluation and testing are essential to ensure the reliability and effectiveness of these new cryptographic techniques.
Challenges in Implementation
While the development of quantum-resistant encryption standards is underway, their implementation poses challenges. Transitioning from existing encryption methods to quantum-resistant alternatives requires careful planning and consideration. Compatibility issues, computational efficiency, and the need for a coordinated global effort to adopt new standards are among the challenges that must be addressed to ensure a smooth transition.
Global Collaboration in Cybersecurity
Given the global nature of cybersecurity threats, international collaboration is vital in establishing and adopting quantum-resistant encryption standards. Standardization bodies, governments, and industry stakeholders must work together to create a unified approach. This collaboration not only facilitates the sharing of expertise but also ensures a consistent and robust response to the quantum threat landscape.
Preparing for the Quantum Era
The journey toward quantum-resistant encryption is a proactive step in preparing for the quantum era. Organizations and entities that handle sensitive information must stay informed about the progress in post-quantum cryptography. A forward-thinking approach involves assessing current encryption practices, understanding the implications of quantum advancements, and planning for the eventual transition to quantum-resistant standards.
Quantum-Resistant Encryption Standards Resource
For those seeking in-depth insights into quantum-resistant encryption standards, Quantum-resistant encryption standards provide a valuable resource. This platform offers updates on the latest developments in post-quantum cryptography, informative articles, and resources to help navigate the evolving landscape of quantum-resistant encryption.
Educating the Cybersecurity Community
As quantum-resistant encryption standards become increasingly critical, educating the cybersecurity community is paramount. Training programs, workshops, and collaborative initiatives can empower cybersecurity professionals to understand the nuances of quantum threats and the measures needed to secure digital information in the quantum era.
Conclusion: Fortifying Cybersecurity in the Quantum Age
The quest for quantum-resistant encryption standards is a crucial chapter in fortifying cybersecurity for the quantum age. As quantum computers advance, the need for resilient encryption becomes more urgent. By staying ahead of quantum threats through research, collaboration, and proactive implementation of quantum-resistant standards, the cybersecurity community can secure a resilient and future-proof digital landscape.